What is a Second Opinion Malware Scanner
A Second Opinion Malware Scanner is just that, a second opinion scanner. No antivirus can detect a full 100% of the Malware. Therefore, it’s always a good practice to have a second opinion malware scanner on your computer. Scan with it regularly to catch those malware that your real-time antivirus may have missed.
The frequency of the scan could be based on your personal preferences or the activity/usage of your computer, for example, if you visit a lot of websites, and different types of websites, i.e., spend a lot of time on the internet, then you could scan your computer on a weekly basis or every fortnight. If you’re not a heavy computer user, maybe once a month is enough.
What’s so Great About these Second Opinion Malware Scanners
The great thing about second opinion scanners is that they run (and use computer resources) only when you open them (on-demand) to scan your computer. So, they never conflict with a real-time antivirus that you have on your system.
Important Points About Second Opinion Malware Scanner & Removal Tools
- It does not have a real-time antimalware protection component i.e., does not scan and detect malware in the real-time or on-access.
- Detects and removes more viruses that one antivirus.
- Removes additional threats and annoyances such as Potentially Unwanted Programs (PUP).
- Using multiple scanning engines is a possibility here to get better detection.
- The malware engine database/signatures may not be updated automatically.
Here are the Best Free Second Opinion Malware/Virus Scanner & Removal Tools for Windows 10
- Zemana AntiMalware (Free)
- Emsisoft Emergency Kit
- Norton Power Eraser
- Malwarebytes Free
- Dr.Web CureIt!
- Comodo Cleaning Essentials
- ESET Online Scanner
- Trend Micro HouseCall
- Panda Cloud Cleaner
- OPSWAT MetaDefender Client
Best Free Second Opinion Malware/Virus Scanner & Removal Tools for Windows
1. Zemana AntiMalware (Free)
Homepage: https://www.zemana.com/AntiMalware
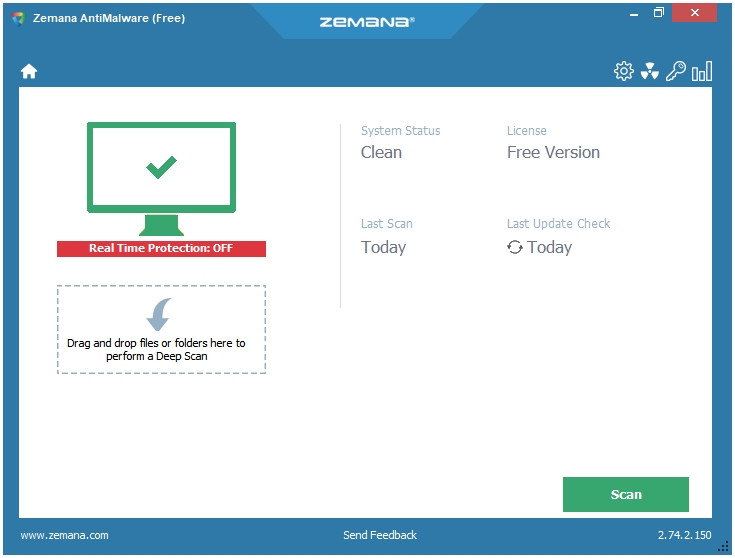
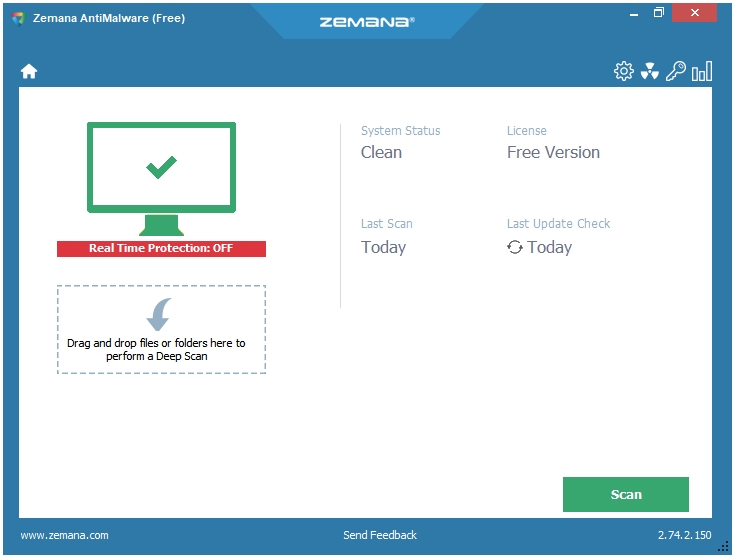
Zemana uses multiple cloud engines to scan and remove malware from your computer. It’s a straightforward malware scanner and removal tool without too many settings and options. It is available in both modes, Installer and Portable. The Installer is of 6 MB, and the Portable version is of about 15 MB in size.
The Scans are quick, and it catches almost everything. You can drag and drop files and folders into the program window to perform the Deep Scan. There is support for the Exclusion feature that lets you exclude the locations that you don’t want Zemana to scan. You can use the Quarantine section to perform additional actions on the detected items. Another feature called Reports displays a log of the scans performed by Zemana on your computer; these reports include the Date and Time of scans, the scan Type, and the Result of the scans.
The program itself is very lightweight. It has a nice flat interface that merges well with the default Windows 10 interface. Program Settings include Create Restore Point, Check for Updates, and Exclusions. The Advanced Settings have some other options and tools such as Detect suspicious (root CA) certificates, Launch Farbar Recovery Scan Tool, etc.
One thing to note here is that Zemana is totally cloud dependent. This is the reason why it is so light on the system and so great in its detection rates. Everything is done by connecting to their cloud network.
2. Emsisoft Emergency Kit
Homepage: https://www.emsisoft.com/en/software/eek/
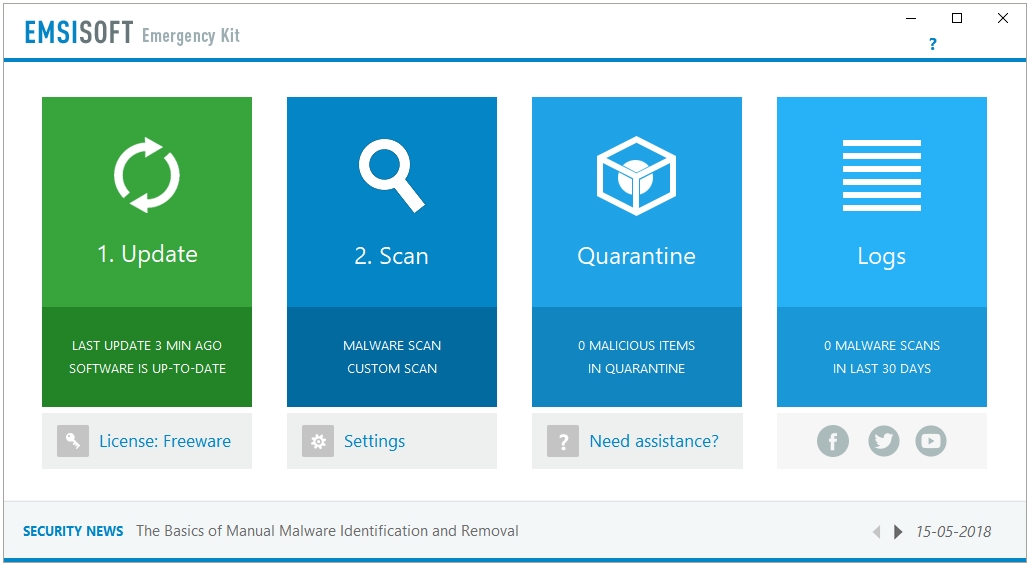
Emsisoft Emergency Kit uses a dual-engine setup. Emsisoft uses Bitdefender’s antivirus signatures along with their own to deliver a stronger detection rate.
It works like a Portable software in a sense that it does not install deeply onto your system. You download the setup file, extract it into a folder, and then run the executable file to start the program. This program can be updated as well, so you have the best of both the worlds. A portable program that updates.
It can be used in both modes – GUI and CLI.
Unlike many other malware scanner and removal tools, Emsisoft Emergency Kit supports different types of scans; you have three scan types to choose from – Quick Scan, Malware Scan, and Custom Scan. The scanning speed varies according to the scan type selected; however, the Malware Scan, one that thoroughly scans the whole computer, is also quick.
Emsisoft Emergency Kit is a great offline scanner, it is not cloud-dependent. So, you can scan, detect, and remove malware even if the network connection is not possible due to any number of reasons. Because it is an offline scanner, it stores the virus signatures on the system, therefore it is not a small program; the setup is more than 300 MB in size.
The user interface is nicely done, Emsisoft Emergency Kit uses a light user friendly interface that integrates well with the Windows UI.
A lot or scan and program settings are available to customize the scanning, detection, and removal process. All of the scanning related features such as Exclusions, Quarantine, and Logs are also available.
3. Norton Power Eraser
Homepage: https://us.norton.com/support/tools/npe.html
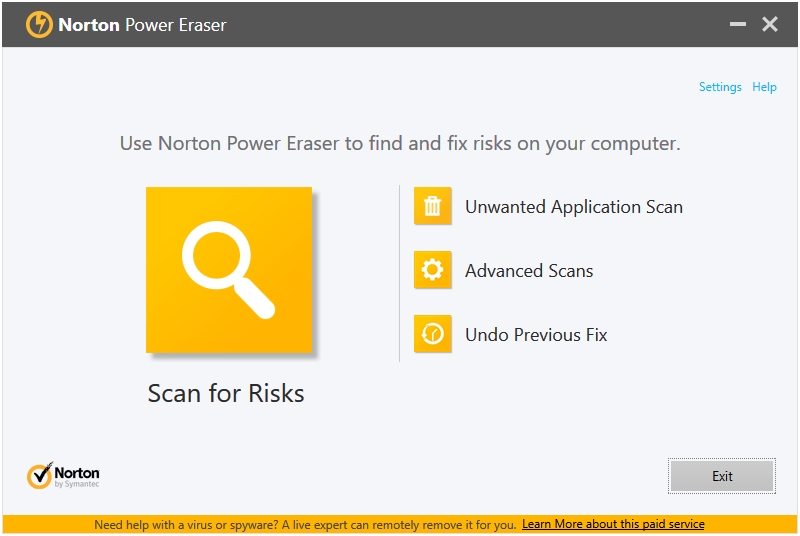
Norton Power Eraser is an advanced malware scanning and removal tool. You can get the gist of their scanning and detection methodology from their tagline that says it Eliminates deeply embedded and difficult-to-detect crimeware.
Norton Power Eraser has the most number of Scan types for a Second Opinion Malware Scanner and Removal Tool. You can run five types of scans using Norton Power Eraser. The big Scan for Risks button performs the Rootkit Scan. The Unwanted Application Scan scans for any Potentially Unwanted Application (PUA) on your system. The scan results are list some False Positives.
The Advanced Scans button takes you to the three types of advanced scans supported by the program, which are – Reputation Scan, System Scan, and Multi-Boot Scan.
The Reputation Scan is great in detecting the zero-day malware that have not be detected by many Antivirus companies. The System Scan performs a full system scan. The Multi-Boot Scan is useful for multi-boot Windows systems; it lets you specify the operating system that you want scanned upon its boot.
A nice feature is Undo Previous Fix, which tries to undo previous repairs made to the system.
Norton Power Eraser is the best option for the new or undiscovered malware because it blocks the files based on their reputation. So, if a file has mixed feedback, but not exactly flagged as a malware, Norton Power Eraser will block it. This also means more false positives, so a double-edged sword. You get this warning about false positive on their product page as well where they say that Norton Power Eraser uses a very aggressive scanning technology to detect and eliminate so it may label some legitimate programs as threats (false positives) in the scan results. But you can easily exclude those program from the scan results.
Norton Power Eraser wound be the best third opinion scanner. Because of its unique method is classifying malicious files, it is not recommended to be used as a single scanner. Use another scanner first, and then run Norton Power Eraser to detect the low reputation files.
It is Portable in nature. It does not install on the system.
4. Malwarebytes Free
Homepage: https://www.malwarebytes.com/
Malwarebytes Free was the first popular computer product with the term malware in their name. Released in 2008 as Malwarebytes Anti-Malware, it gained positive response, and quickly became a must-have tool in computer repair toolkits. It is the only product or Company in this list that became popular only because of a Second-Opinion Malware-Scanner program, and not an Antivirus, an Internet Security or a Total Security product.
It has evolved into a much bigger program. Now Malwarebytes offers real-time protection as well, and the scanner component that made Malwarebytes so popular is just one of the components of this program. Because of a larger program and more modules, it is a little heavy on the system. You cannot get a scanner-only program now, one has to download the full Malwarebytes program that comes with 14-day trail real-time protection. However, you can disable the Trial license, and use it only as an on-demand malware scanner and removal tool.
It is not available as a Portable program, only as an Installer; the installer size is about 75 MB. It works like a proper antivirus without the real-time protection. It supports Automatic Updates, you just have to install it once, and Scan anytime you want. Malwarebytes also has an option to integrate into the Windows Context Menu, a great option to have if you want to scan specific files or folders. Malwarebytes does not rely on the Cloud to work; it downloads the anti-malware signatures on the system, and hence can be used as an Offline scanner.
Two Scan Types are available to the Free users – Threat Scan and Custom Scan; the third type, Hyper Scan, is only available in the Premium version. The Threat Scan is a thorough scan whereas the Custom Scan lets you specify locations that you want to scan. The Hyper Scan checks the Memory and the Startup Objects for any active malware.
The Free version lets you use set up one Scheduled Scan. The Exclusion and Quarantine sections are also present. Malwarebytes is great are detecting Potentially Unwanted Programs (PUPs), and other changes made to the system files and settings.
5. Dr.Web CureIt!
Homepage: https://free.drweb.com/cureit/?lng=en
Dr.Web CureIt! Is a famous malware scanning and removal utility provided by Dr.Web, one of the oldest computer security and anti-malware company. They do not provide any real-time protection products for free. However, they do have a great quality free malware scanning and removal toolkit. Their rescue disk is very polished, and their scanner tool is also very properly done.
It is Portable is nature, you do not need to install it, download the setup file, and double-click to start using it. The file size is of about 160 MB. It does not update, so you need to download new version to get the latest virus definitions.
The scan is called Express Scan by default, and it is really quick at scanning. It can scan Boot sectors of all disks, RAM, Boot disk root folder, Windows system folder, User folders, Temporary files, System Restore points, and it can also search for Rootkits.
Some malicious programs can block and forcefully close antivirus and second opinions scanners; you can select the option Protect Dr.Web CureIt! operation to prevent that from happening.
There are extensive settings for specifying Actions for neutralizing each kind of malware, for example, you can specify which actions to take upon detecting an Adware, a Riskware, or a Suspicious file.
If there are some files and folders that you don’t want Dr.Web to scan then you use the Exclusions feature to do that.
6. Comodo Cleaning Essentials
Homepage: https://www.comodo.com/business-security/network-protection/cleaning-essentials.php
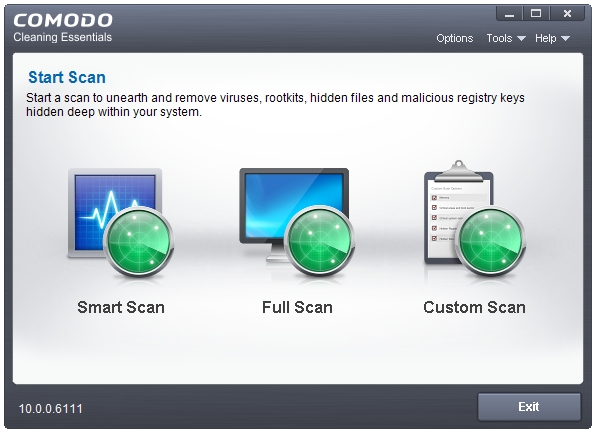
Comodo Cleaning Essentials is a portable toolkit that comes in a Zip archive, which is about 30 MB in size. It has the option to Update, so don’t need to download the latest build every time you want to perform a scan.
The Toolkit comes with three portable tools – Comodo Cleaning Essentials Scanner, Comodo Autorun Analyzer, and KillSwitch.
Comodo Cleaning Essentials Scanner supports three types of Scans – Smart Scan, Full Scan, and Custom Scan. The Smart Scan looks only at the place that are most vulnerable to malware attacks. The Full Scan is a full system sscanthat scans all of your computer and files. The Custom Scan lets you scan only the selected locations. You can scan Memory, Critical areas and boot sector, Hidden registry objects and services, and Hidden files and folders as well. Scanning related features such as Quarantine and Logs are available. You can exclude locations in the Custom Scan.
Under Options, you can find that three forms of malware scanning technologies used in the Comodo Cleaning Essentials Scanner – MBR Scanner, Virus Scanner, and CAMAS (Comodo Automated Malware Analysis (CAMAS)). The Tools tab has shortcuts to KillSwitch and Autorun Analyzer.
COMODO KillSwitch is a feature-rich Task Manager alternative to the Windows Task Manager. You can kill or suspend the shady processes by clicking the Kill All Untrusted Processes, or Suspend All Untrusted Processes button in the KillSwitch tab in the program menu bar.
The Options tab has the option called Replace Task Manager that lets you replace KillSwitch with the Windows Task Manager. Here, you also have options to enable or disable the Tray Icons, configure Symbols, Highlighting; and select the program Language.
You can configure how KillSwitch shows you the Processes, Applications, and Services by clicking on the View tab in the program menu bar, and then selecting either Show Only the Untrusted Images in Memory, or Show Only Untrusted Processes.
The Tools tab has links to the other tools provided in the toolkit by Comodo such as the Comodo Cleaning Essentials scanner, Autorun Analyzer, etc. Various other security related plugins can also be found her such as Quick Repair, Program Usage Analyzer, Find Handles or DLLs, and Verify File Signature.
All of the tools available in the Tools tab, plus some more can be accessed directly through the program dock. These tools are: Start COMODO Cleaning Essentials, Run Autorun Analyzer, Quick Repair, Program Usage Analyzer, Find Window, Find Handles or DLLs, Run, and System Information.
Comodo Autorun Analyzer lists all kinds of Autoruns fond on your system. You can easily see the dangerous or suspicious autorun items by selecting the Hide Trusted Entries option present in the View tab. Under the Entry tab, there are various options for each autorun item such as Delete, Copy, etc. You can quickly switch between users, and analyse the autoruns of other users through the User tab.
7. ESET Online Scanner
Homepage: https://www.eset.com/int/home/online-scanner/
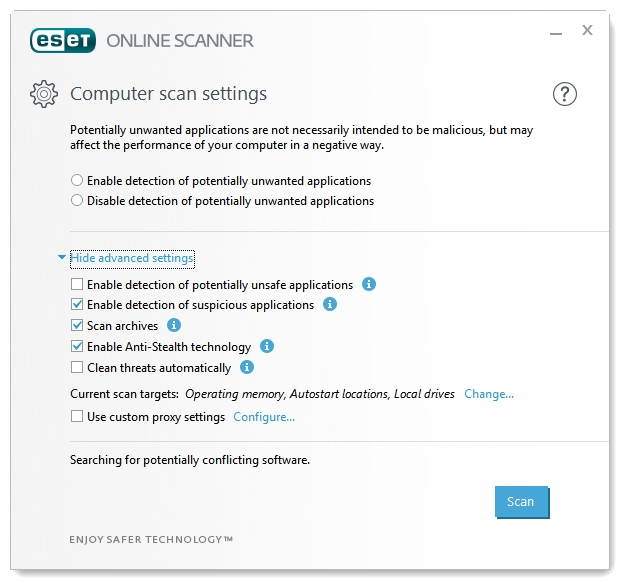
ESET Online Scanner is a free malware scanner and removal tool by ESET. It is a portable and completely cloud dependent program. Download the program file, and run it to start the scanning and removal process.
ESET Online Scanner uses the ESET’s powerful antivirus database, which is also used in their NOD32 Antivirus, to detect and remove all kinds of malware by performing in-depth scanning of the system.
By default, it only shows you two scan settings – Enable or Disable detection of potentially unwanted applications. Click the Advanced settings link to access more scan settings. Here you can see that you have options to Enable or Disable the detection of potentially unsafe applications, and suspicious applications.
Scanning for archives can also be enabled or disabled from here. The Anti-Stealth technology is enabled by default; it scans for active Rootkits on the system.
The Current scan targets: option lets you specify the locations in the computer that you want ESET Online Scanner to scan. By default, all of the Drives/Partitions, Operating memory, and Autostart locations are selected. It scans for Boot sector and Registry as well.
8. Trend Micro HouseCall
Homepage: https://www.trendmicro.com/en_in/forHome/products/housecall.html
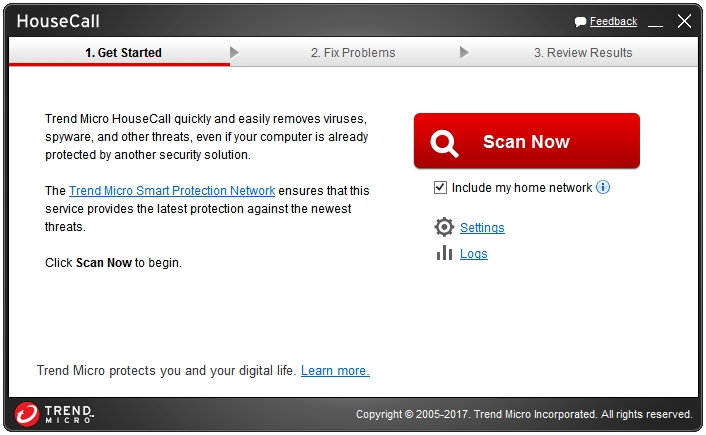
Trend Micro HouseCall is one of the oldest free scanning and removal anti-malware tools. It is a portable application that can run without installing it. Because it is cloud-based, it does take much disk space on your computer.
The Trend Micro HouseCall Settings window has two options – Scan Type and Smart Feedback. Three types of scans are possible with HouseCall – Quick scan, Full system scan, and Custom scan. The Smart Feedback windows lets you enable or disable the Trend Micro Smart Feedback service, which sends the real-time threat information to the Trend Micro Smart Protection Network for analysis.
The Logs button on the main window lets you see the past scan results. The information is displayed in five columns – File, Threat, Type, Risk, and Action. You can undo the Actions taken on a malware by clicking the Restore button. It can be handy in case of a false positive.
The scans made by HouseCall are thorough. It detects and fixes all kinds of malware – viruses, worms, spyware, and other malicious threats thanks to its strong anti-malware database. It is able to find deep hidden processes, and potentially unwanted programs and services.
9. Panda Cloud Cleaner
Homepage: https://www.pandasecurity.com/usa/homeusers/solutions/cloud-cleaner/

Panda Cloud Cleaner uses their technology called ActiveScan Cleaner to scan and remove malware from infected Windows computers. As the name suggests, Panda Cloud Cleaner is a cloud-based malware scanner and removal tool, hence very small-sized and light on the system. It is available in both versions, Installer and Portable. It scans the most important locations, and other system files that malware are expected to attack. Panda lets you Analyse the whole computer for malware or only some selected locations.
Panda Cloud Cleaner is very versatile at detecting the types of malware. The scan results display the items in the following three categories – Malware & PUPs Found, Unknown Files & Suspicious Policies, and System Cleaning. The Malware & PUPs Found sections lists and cleans the various kinds of Malware, Potentially Unwanted Programs, Registry Entries, and other harmful Files found on the system. The Unknown Files & Suspicious Policies section lists and cleans the Broken Links found on the system such as Files, Shortcuts, Tasks, and other obsolete Registry Entries. The System Cleaning section lists and cleans the Temporary Internet Files created by various web browsers on the system.
The Advanced Tools button placed at the menu bar of the program gives you access to some of the more advanced tools that Panda has to offer. There are Kill all processes, Unlock files, and Send files to Panda. The Advanced options gives to an option to scan your computer for Rootkits at your next computer boot using Panda’s special boot mode called Trusted Boot. Click the Activate trusted boot scan option to enable the Rootkit scan.
10. OPSWAT MetaDefender Client
Homepage: https://www.opswat.com/free-tools/free-malware-analysis-tool
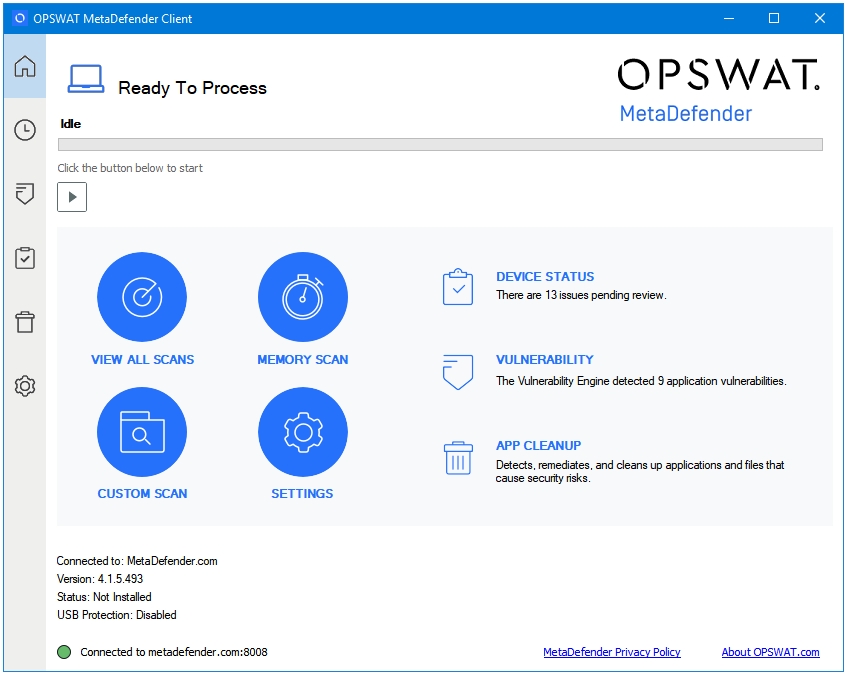
OPSWAT MetaDefender Client is the most feature-rich second opinion malware scanner and removal tool. They also have a Commercial Version, which is aimed at the Enterprises. OPSWAT MetaDefender Client is a portable software.
It uses 36 anti-malware engines (at the time of writing this article) to scan your computer. Because it uses so many anti-malware engines, there are bound to be some false positives.
In case threats are detected on your computer, you can easily find out which engines detected those threats are which did not just by clicking on that detected item in the scan results summary. At the bottom, you can see a list the anti-malware engines used, and their detection result for the selected item. If only 1 out of the 36 engines detected a malware then that could be a case of a false positive.
OPSWAT MetaDefender Client looks and feels a lot like Windows Defender i.e. it integrates into the Windows default theming very well. It displays all of its features in the following six tabs – Home, All Tasks, Vulnerability, Device Status, App CleanUp, and Settings.
- The Home tab is the home screen of the program, and shows the most important items to the user.
- The All Tasks tab lists all or your scans and their results.
- The Vulnerability tab further displays different types of vulnerabilities in the following four tabs – OS Vulnerabilities, App Vulnerabilities, Available Updates, Other Products.
- The Device Status tab shows the status of the applications related to the following components on your computer – Antimalware, Backup and Storage, Encryption, Device Information, Other Category. Clicking on each app shows important status and information about that app. Such as in the Antimalware section, clicking on an app shows two things – Virus Definition Database, and Last Scan Time.
- The App CleanUp tab lets you uninstall the unwanted apps. It automatically recommends you to uninstall some apps in the following two tabs – Automatic Uninstall, Manual Uninstall. Uninstall only if you are sure that that app is not needed anymore.
- The Settings tab lets you access the settings of the program; most of the settings are for their Business version.
What’s important about this tool is that it is developed and maintained by OPSWAT, a cyber-security solutions company that makes software for identifying, detecting, and remediating threats in the enterprise networks.